FIN Scan ilişkin “saklı” frameler olağandışıdır çünkü hedef makinaya ilk TCP el sıkışması olmadan gönderilirler.
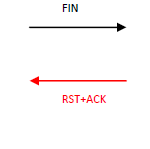
Kaynak makinanın göndereceği FIN bayraklı paket, hedef makinanın kapalı bir portuna gelirse hedef makina RST + ACK bayraklı paket döndürecektir.
Eğer port açık olursa hedef makinadan herhangi bir tepki dönmeyecektir :
Bu taramayı gerçekleştirmek için aşağıdaki komut kullanılmalıdır :
nmap -sF -v [Hedef_IP]
nmap -sF -v 192.168.1.2
at 2010-08-01 18:39 EEST
Initiating ARP Ping Scan at 18:39
Scanning 192.168.1.2 [1 port]
Completed ARP Ping Scan at 18:39, 0.02s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 18:39
Completed Parallel DNS resolution of 1 host. at 18:39, 0.02s elapsed
Initiating FIN Scan at 18:39
Scanning 192.168.1.2 [1000 ports]
Completed FIN Scan at 18:39, 4.35s elapsed (1000 total ports)
Nmap scan report for 192.168.1.2
Host is up (0.00085s latency).
Not shown: 995 closed ports
PORT STATE SERVICE
22/tcp open|filtered ssh
53/tcp open|filtered domain
80/tcp open|filtered http
111/tcp open|filtered rpcbind
2049/tcp open|filtered nfs
FIN
MAC Address: 00:0C:29:D7:D3:65 (VMware)
Read data files from: /usr/local/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 4.56 seconds
Raw packets sent: 1075 (42.988KB) | Rcvd: 997 (39.868KB)